Penetration Testing
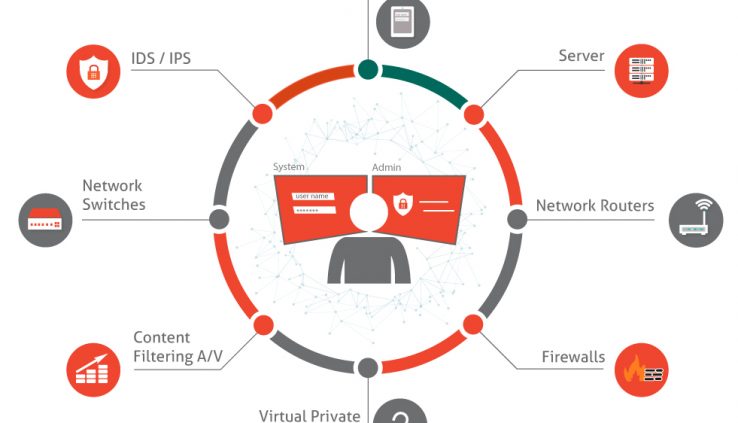
Time and again it has been established that organizations are forced to spend millions of dollars to recover from a security breach because of lost opportunities & remediation efforts.
In Penetration testing or Pen-Testing we conduct a series of activities, which help you identify and exploit security vulnerabilities. It gives you clear picture of the effectiveness or ineffectiveness of the security measures that have been implemented.
It subjects systems to real life security tests. The benefit of penetration testing is to reach beyond a vulnerability scan test and discover different weaknesses and perform a much more detailed analysis. The organization opting for Penetration testing will get detailed information on the actual as well as exploitable security threats and identification of existing and potential vulnerabilities quickly and accurately.